Our anonymization technologies create trust when exchanging sensitive data.
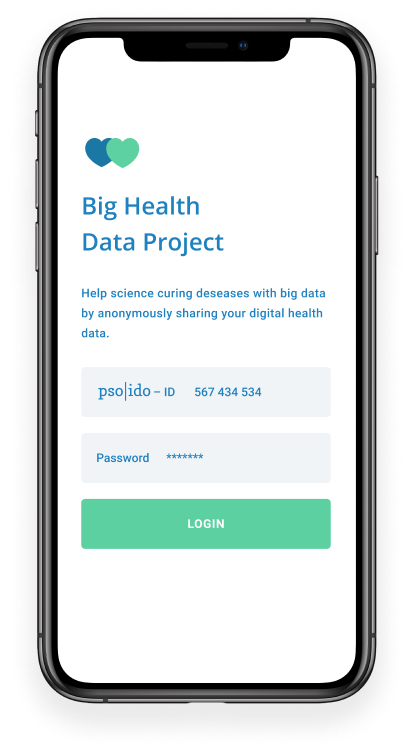
Anonymous Authentification
We solve the contradiction between anonymity and differentiability.
The protection of privacy through anonymous, aggregated data or a differentiated analysis of profiles – an apparently irreconcilable contradiction. With a unique decoupling of real identities to virtual IDs, we solve this knot, the pseudonym becomes anonymous for the first time.
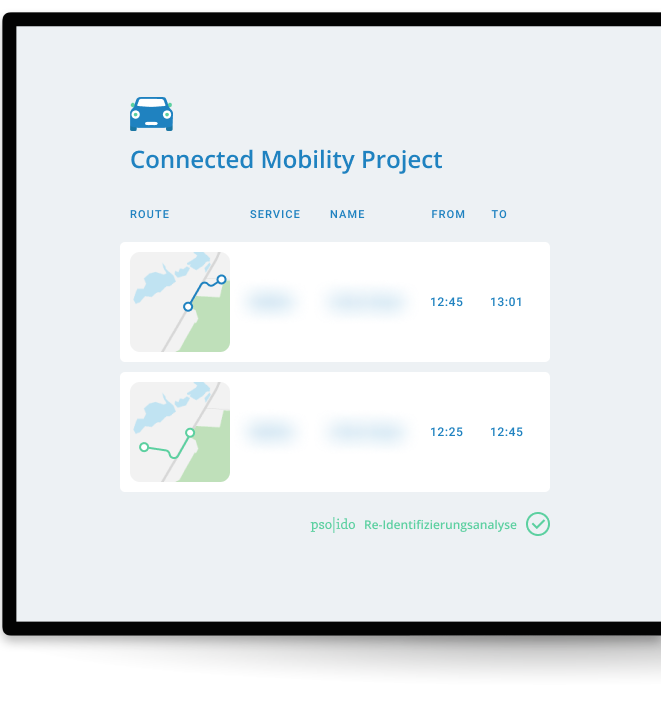
Adaptive Anonymization
We find the
sweet spot between privacy and utility.
Our automated methods allow data sets to be iteratively anonymized. Step by step, data fields are alienated and restored until the exact point is reached at which it is no longer possible to draw conclusions about a real entity. Due to the anonymization, data records remain outside the territory of the GDPR and may be shared with third-party providers without further consent.
We say: The GDPR does not limit, it enables.
As staunch supporters of European data protection standards, we are passionate about developing solutions for the compatibility of privacy and data analysis. So far, data-based business models have often failed due to the distrust of private individuals and companies among one another. The GDPR creates the necessary trust here, which is necessary for the self-determined use of sensitive, but anonymized data. We want to help shape this future.